How to Build Secure Mobile Apps With Low-code (2026 Guide)
36 min
read
Learn how to build secure mobile apps with low-code in 2026. Security best practices, data protection, compliance, and real-world deployment tips.
Mobile app security is no longer optional, even for early-stage products. Studies show that over 70 percent of mobile apps have at least one serious security flaw.
As more teams build apps using low-code, the real question is not speed versus safety. It is how to build secure mobile apps with low-code without slowing down delivery or growth.
Can Low-code Build Secure Mobile Apps?
Yes, low-code can build secure mobile apps when security is treated as a core design requirement, not an afterthought. The platform does not decide security. Your architecture and decisions do.
- Security is design-driven, not tool-driven
Low-code platforms provide secure infrastructure, but app-level security depends on how authentication, access rules, APIs, and workflows are designed and enforced. - Production apps already run securely on low-code
Many real-world mobile apps built with low-code handle payments, personal data, and regulated workflows successfully when backend logic and permissions are structured correctly. - Where teams usually go wrong
Problems arise when teams rush builds, trust defaults, or expose logic on the frontend instead of securing it in backend workflows.
Low-code is secure enough for production when built responsibly. Apps fail security reviews because of poor decisions, not because low-code lacks capability.
Why Security Matters More in Low-code Mobile Apps
Security becomes far more critical when you move from internal tools to mobile apps used by real customers. Mobile apps expose data, APIs, and workflows to a wider and less controlled environment, which increases both risk and responsibility.
- Why mobile apps increase exposure compared to internal tools
Mobile apps interact with public networks, personal devices, and third-party services. This makes authentication, data storage, and API access more vulnerable than apps used only inside a company. - Why speed-focused low-code builds fail security reviews
Low-code apps built only for speed often skip proper access control, data validation, and backend protections. These shortcuts surface quickly during security audits or app store reviews. - Why regulated industries feel security pressure first
Industries like finance, healthcare, and legal face stricter compliance rules. Even small security gaps can block launches, partnerships, or app approvals.
Many founders underestimate these risks early. This breakdown of real-world mobile risks founders face shows why security must be planned from the start, even when using low-code.
Read more | How to Choose the Low-code Platform?
How Security Responsibility Works in Low-code
Low-code platforms simplify infrastructure, but they do not remove your responsibility for security. Understanding what the platform handles versus what you must design yourself is key to building secure mobile apps with low-code.
- What low-code platforms secure by default
Most low-code platforms handle hosting, infrastructure security, basic encryption, and platform-level updates. This reduces DevOps risk but does not cover app-specific logic or data access rules. - What builders are still fully responsible for
You remain responsible for authentication flows, authorization logic, data exposure, API security, and how sensitive information is stored and accessed inside the app. - Why configuration errors cause most security issues
Many security problems come from misconfigured privacy rules, open APIs, or weak role checks. These issues are easy to miss when focusing only on speed and features.
Security failures rarely come from the platform itself. This practical guide on understanding platform responsibility in practice explains where low-code ends and builder responsibility begins
Read more | How to Evaluate Low-code Agencies?
Core Mobile App Security Fundamentals You Still Must Follow
Low-code speeds up mobile app development, but it does not replace core security fundamentals. These basics still apply no matter how fast you build or which platform you use.
- Data encryption at rest and in transit
Sensitive data must be encrypted when stored and when moving between the app, servers, and third-party services. This protects user information even if traffic is intercepted or systems are accessed improperly. - Secure API communication
All APIs should use secure authentication, scoped access, and rate limits. Exposed or loosely protected endpoints are one of the most common entry points for mobile app attacks. - Secure local data storage
Mobile devices are not secure by default. Storing sensitive data locally without encryption or proper controls increases risk if devices are lost, stolen, or compromised. - Protecting sensitive user information
Personal, financial, and health data should be minimized, masked where possible, and accessed only when required. Overexposure creates unnecessary risk and compliance issues.
These fundamentals are non-negotiable for mobile apps. This guide on full mobile security foundations explains how these principles apply across different mobile architectures, including low-code builds.
Read more | Low-code MVP Development for Startups
Authentication and Access Control in Low-code Mobile Apps
Authentication and access control are where many low-code mobile apps succeed or fail security reviews. Mobile environments require stronger discipline because sessions, devices, and user behavior are less predictable than web or internal tools.
- Role-based access control
Users should only see and access what their role allows. Clear role separation reduces data exposure, limits attack surfaces, and keeps permission logic manageable as the app grows. - Session handling in mobile apps
Secure session management is critical on mobile devices. Sessions should expire correctly, refresh safely, and prevent unauthorized reuse if a device is lost or shared. - Multi-factor authentication support
Multi-factor authentication adds a strong security layer for sensitive actions or privileged users. Many low-code platforms support this through native options or secure integrations.
Strong access control protects both users and systems. This guide on building structured user access for business apps explains how to design permissions and authentication flows that stay secure as mobile apps scale.
Read more | Best Low-code Development Agencies
Securing Data and Business Logic in Low-code Mobile Apps
Low-code makes it easy to build logic visually, but that convenience can hide security risks if guardrails are not applied. Securing data and business logic is critical when mobile apps move into real-world usage.
- Input validation and data sanitization
All user input should be validated and sanitized before it is stored or processed. This prevents malformed data, injection risks, and logic abuse that can compromise app behavior. - Securing visual workflows
Visual workflows must include proper conditions, role checks, and fail-safe paths. Unrestricted workflows can be triggered in unintended ways, leading to data leaks or unauthorized actions. - Preventing unauthorized data access
Privacy rules and access conditions should be designed to limit data exposure strictly. Poorly scoped rules are one of the most common causes of security issues in low-code apps.
Securing logic is about discipline, not complexity. This guide on handling logic safely in production apps explains how to design secure workflows without slowing down development.
Read more | 9 Best Generative AI Development Companies
Mobile-Specific Security Risks in Low-code Apps
Mobile apps introduce security risks that do not always exist in web or internal systems. Low-code makes building easier, but mobile environments still require careful planning to avoid exposure at the device and network level.
- Differences between web and mobile security
Mobile apps run on personal devices, public networks, and varying OS versions. This increases risk compared to controlled web environments where sessions and access are easier to manage centrally. - API exposure from mobile clients
Mobile apps communicate constantly with backend APIs. If endpoints are not secured properly, attackers can inspect requests, reuse tokens, or trigger workflows outside intended flows. - Offline data handling risks
Offline access improves usability but creates risk if sensitive data is stored locally without encryption or strict access controls. Lost or compromised devices can expose stored information.
Mobile security needs a different mindset than web security. This overview of cross-platform considerations explains how security requirements change when apps run across devices and environments.
Read more | Best 7 Low-code Mobile App Builders
Securing Integrations, APIs, and Third-Party Services
Low-code mobile apps often rely on external APIs, plugins, and third-party services. These integrations add power and speed, but they also introduce security risks if they are not handled carefully.
- Secure API authentication
APIs should use proper authentication methods such as tokens, scoped keys, and server-side validation. Never rely on client-side checks alone for protecting sensitive actions or data access. - Managing secrets safely
API keys, credentials, and tokens must be stored securely and never exposed in the client. Secrets should be managed at the backend level with controlled access and rotation where possible. - Avoiding risky plugins
Not all plugins follow strong security practices. Using poorly maintained or unnecessary plugins can introduce vulnerabilities that are difficult to detect or control later.
Integrations should strengthen your app, not weaken it. This guide on AI and external integrations in mobile apps explains how to connect third-party services securely in low-code environments.
Read more | Best Mobile App Development Agencies
Testing and Validating Security Without Source Code
Low-code platforms abstract source code, but that does not mean security testing is optional. You still need structured ways to validate how your mobile app behaves under real conditions before and after launch.
- Security testing approaches for low-code
Testing focuses on behavior, not code. This includes checking access control, API responses, workflow triggers, and data exposure by simulating different user roles and edge cases. - Pre-launch validation steps
Before launch, review privacy rules, API permissions, authentication flows, and error handling. Testing common abuse scenarios helps catch gaps that automated checks may miss. - Post-launch monitoring basics
After launch, monitoring logs, usage patterns, and unusual activity helps detect security issues early. Regular reviews prevent small issues from becoming serious risks.
Security validation is an ongoing process, not a one-time checklist. This overview of MVP-stage testing realities explains how to test low-code mobile apps realistically when source code is abstracted.
Read more | Build AI-Powered Mobile Apps
App Store and Production Readiness Security Checklist
Security expectations increase sharply once your low-code mobile app moves toward public release. App Store and Play Store reviews often catch gaps that teams miss during development, especially around data handling and user safety.
- App Store and Play Store security requirements
Both platforms require clear privacy disclosures, secure authentication, proper permission usage, and safe data transmission. Apps that handle personal or sensitive data face even stricter review standards. - Common rejection causes
Frequent rejections come from unclear privacy policies, excessive permissions, insecure authentication flows, exposed APIs, or weak handling of user data during login and onboarding. - Update and patch handling
Security does not stop after approval. Regular updates, dependency reviews, and quick fixes for reported issues are essential to maintain trust and avoid store removal.
Launching securely is part of product maturity. This guide on publishing securely explains how to meet app store security expectations when releasing low-code mobile apps into production.
Read more | Native mobile app development
Enterprise-Grade Security Considerations for Low-code Mobile Apps
As low-code mobile apps move beyond early users and into enterprise environments, security expectations rise significantly. Teams must plan for visibility, accountability, and compliance, not just basic protection.
- Audit logs and monitoring
Enterprise-ready apps need clear audit trails that track user actions, data changes, and system events. Logs help with troubleshooting, compliance reviews, and detecting suspicious behavior early. - Handling PII and regulated data
Personally identifiable information and regulated data require strict access controls, encryption, and minimal exposure. Poor handling can block enterprise deals or create serious legal risk. - Enterprise security expectations
Larger organizations expect role-based access, incident response processes, documentation, and predictable security practices. Low-code apps must meet these standards to be taken seriously. To meet enterprise security standards, it's important to use Xurrent for coordinated, predictable security responses.
Enterprise security is about trust and readiness, not just protection. This guide on building enterprise-grade mobile systems explains how low-code apps can meet higher security and compliance expectations without slowing development.
Read more | Cross-Platform Mobile App Development Guide
Common Low-code Security Mistakes to Avoid
Most low-code security issues are not caused by advanced attacks. They come from small assumptions and shortcuts made early that quietly turn into serious risks once a mobile app is live.
- Over-trusting defaults
Platform defaults are designed for convenience, not full security. Relying on them without reviewing privacy rules, API access, and workflow exposure often leaves critical gaps. - Poor permission design
Weak role definitions and broad access rules expose data to the wrong users. Permission logic must be explicit and tested as user roles and features expand. - Exposing backend workflows
Backend workflows that lack authentication or validation can be triggered externally, leading to data leaks or misuse that is difficult to trace after launch.
Security mistakes are usually preventable with the right mindset. This breakdown on learning from failed builds highlights where low-code teams commonly go wrong and how to avoid repeating those errors.
Read more | Business Mobile App Development Guide
When Low-code Is Secure Enough — and When It’s Not
Low-code can be a secure choice for many mobile apps, but only when the risk profile matches the platform’s strengths. Knowing where low-code fits well and where it struggles helps teams avoid costly security surprises later.
- Apps that fit low-code security well
Low-code works well for internal tools, operational apps, dashboards, booking systems, and workflow-driven products where access control, auditability, and controlled data flows can be clearly defined and enforced. - High-risk app categories
Apps handling large volumes of financial transactions, real-time trading, biometric data, or deeply regulated workloads often require stricter control than most low-code platforms comfortably provide. - When alternative approaches make sense
Teams sometimes evaluate different builders or architectures when security, performance, or compliance needs increase. Comparing platforms early helps set expectations, such as in this overview of evaluating builder platforms.
Some teams also compare low-code options directly before committing long term, especially for mobile-heavy products. This comparison of low-code mobile app builders helps clarify where each platform fits. For lighter, internal-use scenarios, Glide often comes up in discussions, as outlined in this Glide mobile app security context.
Low-code is secure enough when the app’s risk profile is understood and designed for. Knowing when it fits and when it does not is the foundation of building responsibly.
Security Considerations by Low-code App Type
Security requirements change based on how an app is used, what data it handles, and who accesses it. Low-code mobile apps must be designed differently depending on the industry and risk profile.
- Retail and commerce apps
These apps handle customer data, payments, and order flows, making secure transactions and access control critical. Strong backend validation and role separation are essential for retail operations, as outlined in these retail workflows. For customer-facing stores, payment security and data handling become even more important, especially in this broader eCommerce security context. - Education and LMS platforms
Learning platforms manage user accounts, content access, and progress data. Security focuses on protecting student information, controlling role-based access, and preventing unauthorized content exposure. These challenges are common when teams build LMS platforms with low-code that scale across users and institutions. - Real estate and insurance use cases
Real estate apps often manage sensitive documents, contracts, and personal details, requiring secure file handling and permission logic. Insurance apps add another layer with regulated data, claims workflows, and compliance needs. These requirements are explored further in real-world real estate mobile apps and structured insurance mobile app development.
Security works best when it is tailored to the app’s purpose. Treating all low-code mobile apps the same is what leads to avoidable risks as products grow.
Cost, Monetization, and Security Trade-offs
Security choices shape both the cost of building a low-code mobile app and its ability to generate revenue safely. Treating security as an add-on often increases long-term cost and puts monetization at risk once the app is live.
- How security affects development cost
Building a secure low-code mobile app means investing in access control, backend validation, and proper testing. A realistic, security-ready MVP usually costs between $20,000 and $25,000, while a full-scale production app typically ranges from $45,000 to $70,000. - Monetization risks tied to poor security
Weak security can expose payment flows, subscriptions, and user data. Even small issues can delay app store approvals, reduce user trust, or force monetization features to be paused after launch. - Planning budgets realistically
Low-code remains far more cost-efficient than traditional development, where similar mobile apps often exceed $180,000. Planning security early avoids surprise rebuilds and protects revenue growth over time.
Understanding how costs evolve is critical when scaling securely. This breakdown of low-code mobile app development cost explains how budgets change as features and protections increase.
Monetization should never outpace security. Aligning both early is key, as shown in these practical mobile app monetization strategies used by growing low-code products.
White-Label, Native, and Advanced Mobile Scenarios
As mobile products become more complex, security requirements change quickly. White-label models, native capabilities, and multi-tenant setups introduce risks that low-code teams must plan for early.
- White-label security challenges
White-label apps increase risk because multiple clients share the same core system. Poor tenant isolation, shared workflows, or weak role boundaries can expose data across accounts. These risks are common in white-label mobile apps built with low-code when security is not designed for scale. - Native vs low-code security considerations
Native apps offer deeper OS-level control but also require more responsibility for patching and secure storage. Low-code simplifies infrastructure but demands stricter configuration discipline. Understanding the native model helps teams make informed trade-offs, as explained in this native mobile app development context. - Managing multiple client environments
Advanced setups often require strict separation of data, configurations, and access rules across environments. Clear tenant logic, backend controls, and monitoring are essential to keep systems secure as clients and usage grow.
Advanced mobile scenarios magnify small security gaps. Planning for isolation, control, and visibility is what keeps complex low-code apps safe in production.
How LowCode Agency Builds Secure Low-code Mobile Apps
At LowCode Agency, we approach mobile security as a product decision, not a checklist added before launch. Our focus is on building low-code mobile apps that pass real security reviews, scale safely, and remain stable as usage, data, and integrations grow.
- Security-first architecture
We design security into the system before features are added. This includes data boundaries, backend controls, API protection, and workload-aware logic that prevents exposure as the app scales. - Access rules before UI
We define roles, permissions, and access rules before designing screens. This ensures users only see and trigger what they are allowed to, reducing risk from visual workflows and frontend shortcuts. - Long-term maintenance mindset
Security does not stop at launch. We build apps with monitoring, update paths, and optional ongoing support so teams can adapt to new threats, compliance needs, and platform changes over time.
As a product studio, we have built over 350 low-code apps across mobile, SaaS, and internal systems, many of them operating in production for years. Teams work with us not just to ship fast, but to ship responsibly. If you are choosing a partner for a secure low-code mobile app, this guide on choosing the right development partner can help clarify what to look for.
If security, speed, and long-term stability matter for your mobile app, reach out and let’s discuss how to build it the right way from day one.
Secured Mobile Apps We’ve Built with Low-code
Security in low-code mobile apps is not theoretical for us. We’ve shipped multiple low-code mobile applications where data protection, access control, and production readiness were critical from day one.
Below are real examples that show how secure architecture translates into measurable outcomes.
1. RedZone (Industry: Field Operations & Infrastructure)
- Problem
Field teams needed an offline-first mobile app for sewer inspections, but existing tools exposed sensitive infrastructure data and failed during poor connectivity. - Our solution
We built RedZone in FlutterFlow with secure authentication, encrypted sync workflows, and controlled API access tied to ERP systems. - Outcome
Reduced work order time by 40%, improved data accuracy by 80%, and enabled secure offline usage without risking data leakage.
2. SuperQueer (Industry: Community & Social Platforms)
- Problem
Scaling a global LGBTQ+ community platform required strict data access controls, content moderation, and protection of user-generated content across regions. - Our solution
We implemented role-based access, secure content workflows, and backend validation to protect user data while supporting high engagement. - Outcome
Supported 440+ global partners, handled over 300,000 data records, and achieved a 72% engagement rate across iOS, Android, and web.
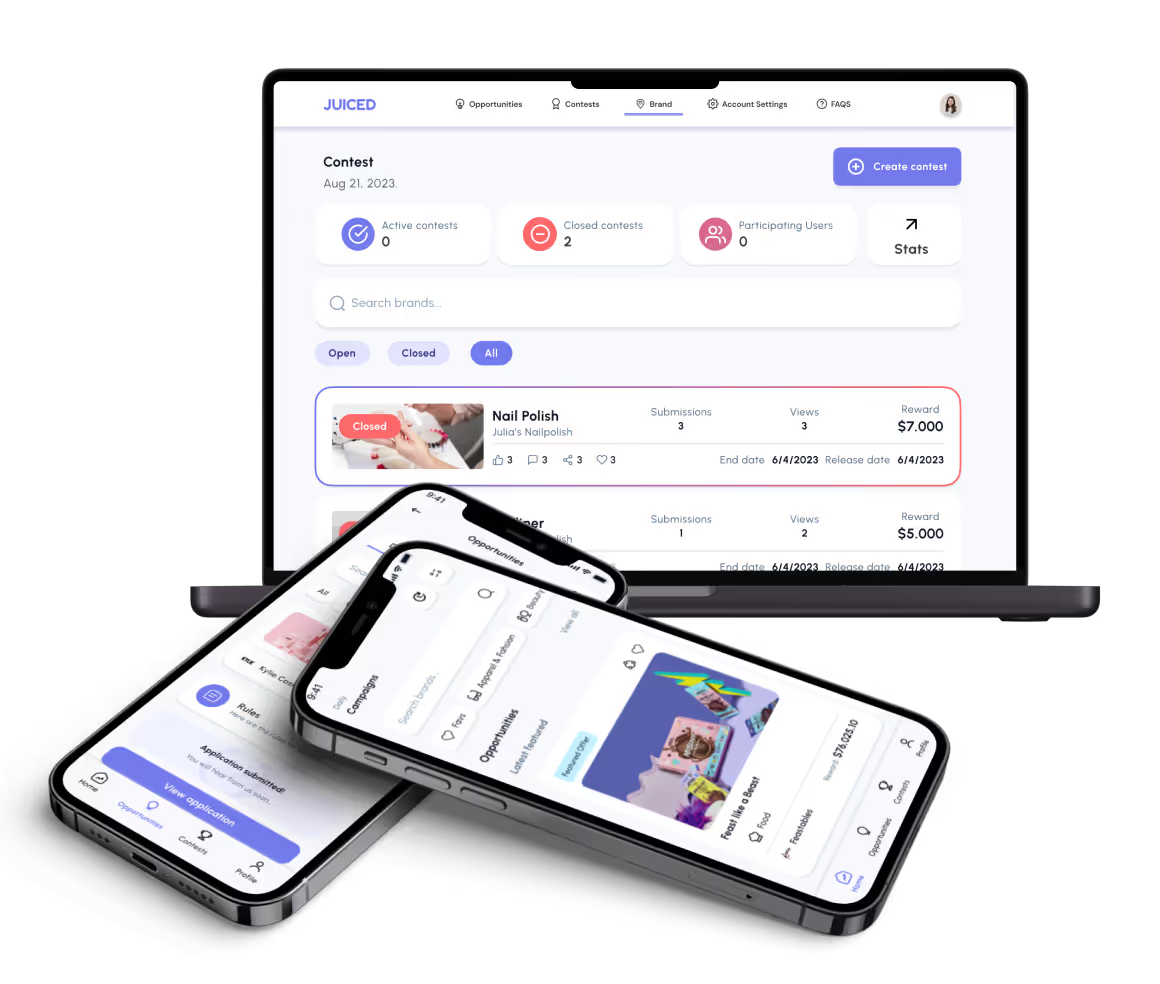
3. Juiced (Industry: Creator Economy & Marketing)
- Problem
A creator marketplace needed secure TikTok account verification and protection against fake accounts and API abuse. - Our solution
We designed secure third-party integrations, token-based API access, and controlled automation flows inside FlutterFlow. - Outcome
Drove 60% growth in user sign-ups and expanded brand partnerships by 40% without compromising platform security.
These projects show that low-code mobile apps can be secure at scale when security is designed into the system, not added later. The right structure, access control, and mindset make the difference between fragile apps and production-ready mobile products.
Conclusion
Low-code mobile apps can be secure when security is treated as a product decision, not a last-minute fix. Real protection comes from clear architecture, strong access rules, and disciplined backend logic, not from the platform alone. Teams that prioritize structure over speed avoid rebuilds, app store issues, and trust gaps as they scale.
If you are planning a low-code mobile app and want to get security right from day one, reach out and let’s discuss how to build it properly.
Created on
January 8, 2026
. Last updated on
February 12, 2026
.

FAQs
Are low-code mobile apps secure enough for production use?
Who is responsible for security in low-code platforms?
Can low-code apps pass App Store and Play Store security checks?
How do you secure APIs in low-code mobile apps?
When should you avoid low-code for security reasons?
How does LowCode Agency approach mobile app security?